
In tandem with the digital age of our times, the lines between the real and virtual worlds are becoming increasingly blurred. Think about your daily life and how it would come to a standstill if you lose access to your digital device or network connectivity. While the dawn of the digital age is well and good, one of the World Wide Web’s (WWW) pain points is the infrastructural flaws of Web2 platforms stemming from their data monetization models. The centralized framework of these models gives rise to risks associated with a lack of transparency about data management, such as undue disclosure.
A notable example is the Cambridge Analytica scandal involving Facebook, in which the personal data of up to 87 million users of the Web2 social media platform was unduly exposed. For all we know, the next victim could be you, me, or any other web user. Web3, as the next iteration of the Internet, maybe the solution for the personal data protection deficiencies of Web2.
Web3 and Personal Data ProtectionIf, like most web users, you prefer to be in control of your personal data, then Web3 is the thing for you. The central tenet of Web3 is user autonomy. In the context of personal data, the element of autonomy for Web3 users means that the users would have the right to decide for themselves the management and usage of their personal data. In line with this agenda, a few concepts and instruments could bring to life the ideals of Web3 when it comes to warranting user autonomy over their personal data. Some of these concepts and instruments are self-sovereign identity (SSI), decentralized identifiers (DIDs), and digital footprint security.
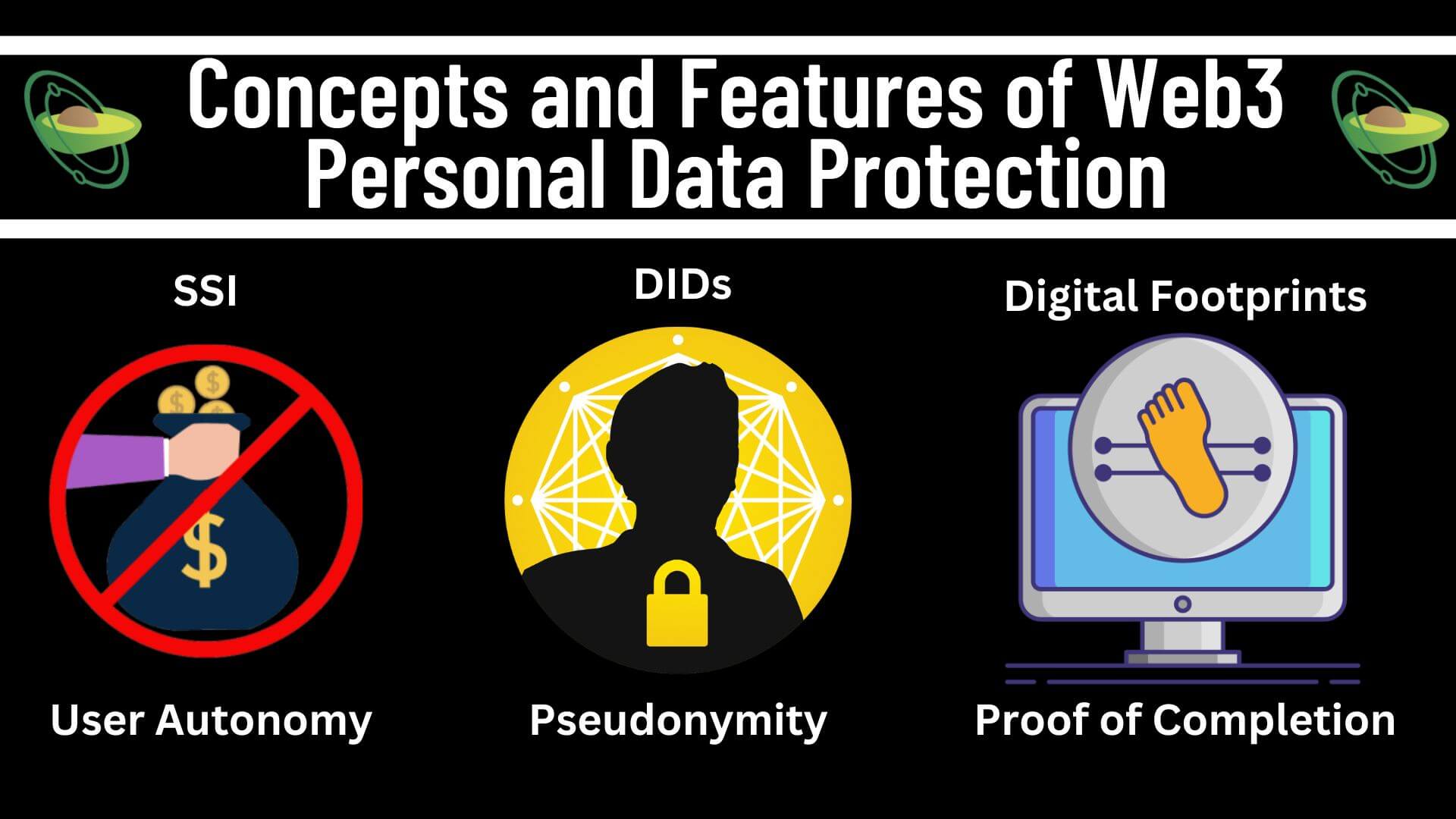 Concepts and Features of Web3 Personal Data Protection (Source: Avocado DAO)
Concepts and Features of Web3 Personal Data Protection (Source: Avocado DAO)
The core idea of SSI is that users ought to have absolute control over the personal data underlying their digital identities. In effect, this means that users should not have to rely on third parties to store, process, and share their personal data.
For example, the identity authentication frameworks of Web2 platforms are such that users have to share their credentials with third parties, namely the platform owners. This need for data sharing with third parties departs from the concept of SSI and contrasts with Web3’s notion of user autonomy.
Decentralized Identifiers (DIDs)In essence, DIDs are pseudo-anonymous identifiers that enable users to verify their digital identities without disclosing their private data or relying upon a centralized intermediary like Facebook or your bank. Users can use their private keys to create a digital signature and apply it to a message like proving their identity to a dApp platform. The dApp platform, such as Uniswap, will match the user’s public key to their digital signature and authenticate the user as the valid owner of the wallet.
- Private keys: A private key is a unique and secret code used to sign and authorize digital transactions. The user must keep the private key secret and never share it with others to protect their DIDs.
- Digital signatures: A mathematical code generated using a private key and applied to a message or transaction. Digital signatures prove authenticity, and the signatory cannot repudiate a signature completed in the past.
- Public keys: A public key is a code derived from a private key. Unlike private keys, the user can share public keys with other parties. Anyone can use the public key to verify a digital signature to prove the authenticity of a message or transaction.
Digital footprints refer to the trail of data and information left behind by web users. These could include online purchases, financial transactions, social media activities, and the completion of online courses. The immutable and tamper-proof nature of blockchain records significantly reduces the risks of undue manipulation or unauthorized alteration by web users of their digital footprints. This paves the way for the concept of Proof-of-Completion (PoC), which entails verifying the successful completion of a task or activity by a web user. The use of PoC allows organizations such as educational institutions and prospective employers to verify that applicants have obtained the necessary skills or knowledge through their participation in online courses and programs.
Implementing Web3’s Personal Data Protection with BlockchainA few examples of real-world implementations of the Web3 concepts described above exist. The examples we want to highlight in this course are Soulbound Tokens (SBTs) and Zero Knowledge Proof (ZKP) protocols.
Soulbound Tokens (SBTs)SBTs use blockchain to power the social identities of individuals in decentralized communities. In essence, SBT is an NFT, which stores the verifiable credentials of its owner. SBTs are also non-transferable and permanently bound to their holding wallets. These qualities enable the SBTs suitable for both the verification of identities and the tracking of reputation. In this way, it would not be possible for web users to dissociate themselves from their real-world identities or for another party to imitate them. SBT helps fulfill the Web3 concept of SSI and digital footprint integrity.
An interesting use case of SBT has come about from the collaboration between Masa Finance and Celo blockchain. Under the collaboration, the 10+ million active wallet holders in the Celo ecosystem would be able to use Masa Finance's protocol to generate a prosperity passport. The passport comes with a host of SBT features including " an authenticated user verification SBT, a credit score SBT, a community reputation SBT and a “.celo” domain name SBT".
Zero-Knowledge Proof (ZKP) ProtocolsThe use of ZKP cryptographic protocols enables the authentication of users’ digital identities by verifying a piece of information without sharing the whole. The main benefit of using ZKP protocols for everyday users is that it allows the verification of digital identities without requiring the disclosure of personal information to the authenticating party. Using ZKP protocols would help mitigate the risks of undue disclosure and security breaches since third parties would not have access to your complete personal information, such as financial information.
Additionally, the use of ZKP protocols would also shorten the time required for the digital identity verification process as it reduces the amount of information needed to be transmitted and verified. These qualities of ZKP protocols help it fulfill the Web3 concepts of SSI and DIDs, securing our digital identities for a safer web.
ConclusionAs our real-world existence is increasingly assimilated with our digital personalities, the issue of personal data protection is set to become increasingly pertinent moving forward. In contrast with the data monetization models of Web2 platforms under which user data are products to be monetized, Web3 deems such data as having the right to be protected. Given the potential of blockchain for personal data protection, it could prove to be the technological enabler that helps secure our Web3 souls.
In this course, we have covered the different ways in which the use of blockchain can help secure our Web3 digital identities. In our next course, The Dollars and Cents of Web3, we are going to discuss the use of blockchain for the financing aspects of Web3 through the cryptoization mechanism.